Top Security Breaches 2026-01-27
Auto-generated 2026-01-27T09:00:27.042839+00:00 (UTC)
-
Why Secrets in JavaScript Bundles are Still Being Missed
Source: The Hacker News | Published: 2026-01-20T10:45:00+00:00 | Score: 19.822
Leaked API keys are no longer unusual, nor are the breaches that follow. So why are sensitive tokens still being so easily exposed?
To find out, Intruder’s research team looked at what traditional vulnerability scanners actually cover and built a new secrets detection method to address gaps in existing approaches.
Applying this at scale by scanning 5 million applications revealed over -
Multi-Stage Phishing Campaign Targets Russia with Amnesia RAT and Ransomware
Source: The Hacker News | Published: 2026-01-24T11:09:00+00:00 | Score: 12.927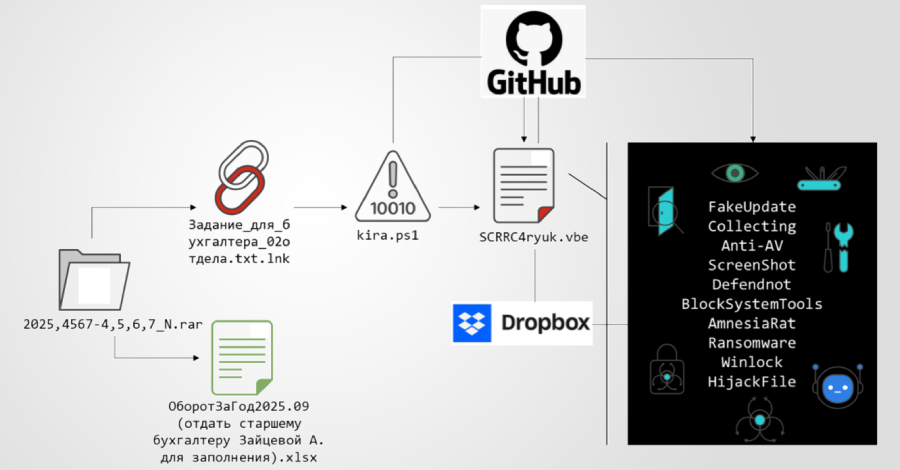
A new multi-stage phishing campaign has been observed targeting users in Russia with ransomware and a remote access trojan called Amnesia RAT.
“The attack begins with social engineering lures delivered via business-themed documents crafted to appear routine and benign,” Fortinet FortiGuard Labs researcher Cara Lin said in a technical breakdown published this week. “These documents and -
Chainlit AI Framework Flaws Enable Data Theft via File Read and SSRF Bugs
Source: The Hacker News | Published: 2026-01-21T09:10:00+00:00 | Score: 12.902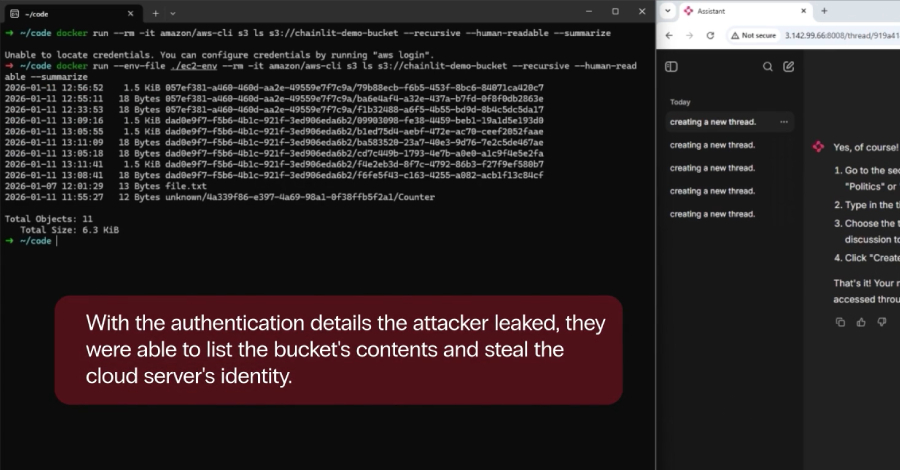
Security vulnerabilities were uncovered in the popular open-source artificial intelligence (AI) framework Chainlit that could allow attackers to steal sensitive data, which may allow for lateral movement within a susceptible organization.
Zafran Security said the high-severity flaws, collectively dubbed ChainLeak, could be abused to leak cloud environment API keys and steal sensitive files, or -
New Osiris Ransomware Emerges as New Strain Using POORTRY Driver in BYOVD Attack
Source: The Hacker News | Published: 2026-01-22T18:00:00+00:00 | Score: 12.412
Cybersecurity researchers have disclosed details of a new ransomware family called Osiris that targeted a major food service franchisee operator in Southeast Asia in November 2025.
The attack leveraged a malicious driver called POORTRY as part of a known technique referred to as bring your own vulnerable driver (BYOVD) to disarm security software, the Symantec and Carbon Black Threat Hunter -
Google Gemini Prompt Injection Flaw Exposed Private Calendar Data via Malicious Invites
Source: The Hacker News | Published: 2026-01-19T17:21:00+00:00 | Score: 12.404
Cybersecurity researchers have disclosed details of a security flaw that leverages indirect prompt injection targeting Google Gemini as a way to bypass authorization guardrails and use Google Calendar as a data extraction mechanism.
The vulnerability, Miggo Security’s Head of Research, Liad Eliyahu, said, made it possible to circumvent Google Calendar’s privacy controls by hiding a dormant -
Evelyn Stealer Malware Abuses VS Code Extensions to Steal Developer Credentials and Crypto
Source: The Hacker News | Published: 2026-01-20T11:48:00+00:00 | Score: 12.275
Cybersecurity researchers have disclosed details of a malware campaign that’s targeting software developers with a new information stealer called Evelyn Stealer by weaponizing the Microsoft Visual Studio Code (VS Code) extension ecosystem.
“The malware is designed to exfiltrate sensitive information, including developer credentials and cryptocurrency-related data. Compromised developer -
Phishing Attack Uses Stolen Credentials to Install LogMeIn RMM for Persistent Access
Source: The Hacker News | Published: 2026-01-23T11:18:00+00:00 | Score: 11.369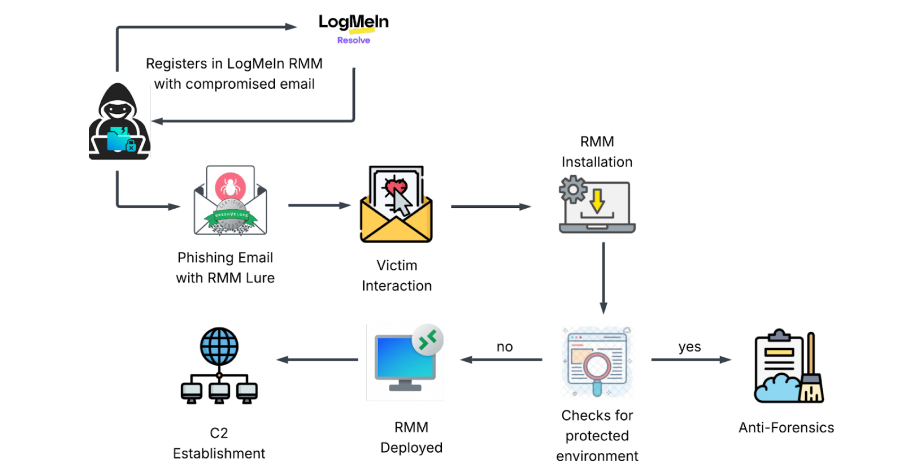
Cybersecurity researchers have disclosed details of a new dual-vector campaign that leverages stolen credentials to deploy legitimate Remote Monitoring and Management (RMM) software for persistent remote access to compromised hosts.
“Instead of deploying custom viruses, attackers are bypassing security perimeters by weaponizing the necessary IT tools that administrators trust,” KnowBe4 Threat -
Microsoft Flags Multi-Stage AitM Phishing and BEC Attacks Targeting Energy Firms
Source: The Hacker News | Published: 2026-01-23T08:25:00+00:00 | Score: 11.333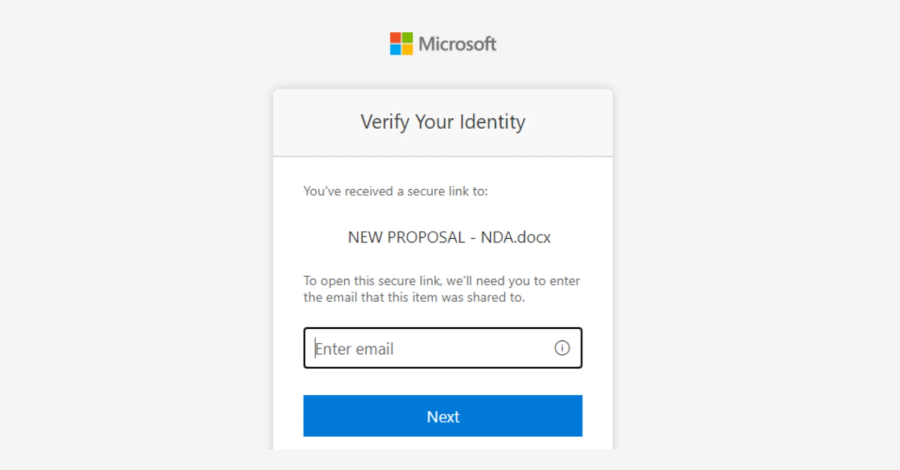
Microsoft has warned of a multi‑stage adversary‑in‑the‑middle (AitM) phishing and business email compromise (BEC) campaign targeting multiple organizations in the energy sector.
“The campaign abused SharePoint file‑sharing services to deliver phishing payloads and relied on inbox rule creation to maintain persistence and evade user awareness,” the Microsoft Defender Security Research Team said.
End of report.
