Top Security Breaches 2026-01-20
Auto-generated 2026-01-20T09:00:34.604655+00:00 (UTC)
-
Ingram Micro says ransomware attack affected 42,000 people
Source: BleepingComputer | Published: 2026-01-19T13:33:45+00:00 | Score: 18.184
Information technology giant Ingram Micro has revealed that a ransomware attack on its systems in July 2025 led to a data breach affecting over 42,000 individuals. […]
-
Hacker admits to leaking stolen Supreme Court data on Instagram
Source: BleepingComputer | Published: 2026-01-19T16:04:14+00:00 | Score: 17.712
A Tennessee man has pleaded guilty to hacking the U.S. Supreme Court’s electronic filing system and breaching accounts at the AmeriCorps U.S. federal agency and the Department of Veterans Affairs. […]
-
CIRO confirms data breach exposed info on 750,000 Canadian investors
Source: BleepingComputer | Published: 2026-01-18T15:17:45+00:00 | Score: 17.137
The Canadian Investment Regulatory Organization (CIRO) confirmed that the data breach it suffered last year impacts about 750,000 Canadian investors. […]
-
AWS CodeBuild Misconfiguration Exposed GitHub Repos to Potential Supply Chain Attacks
Source: The Hacker News | Published: 2026-01-15T19:31:00+00:00 | Score: 16.931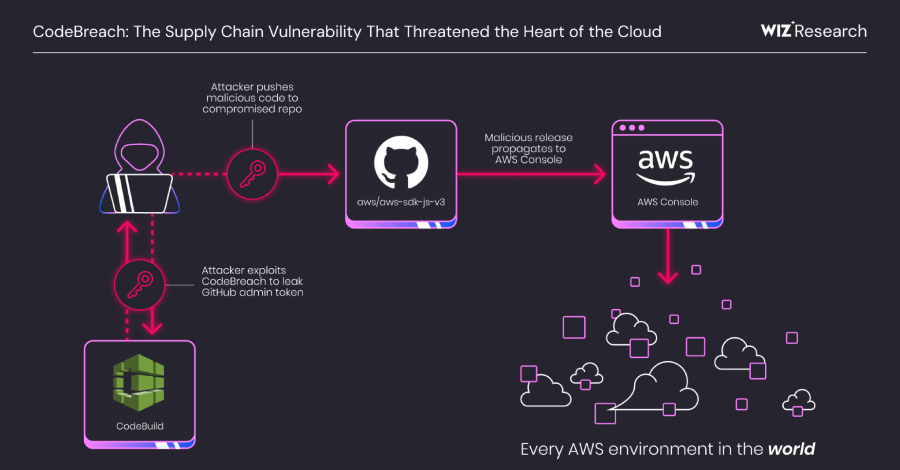
A critical misconfiguration in Amazon Web Services (AWS) CodeBuild could have allowed complete takeover of the cloud service provider’s own GitHub repositories, including its AWS JavaScript SDK, putting every AWS environment at risk.
The vulnerability has been codenamed CodeBreach by cloud security company Wiz. The issue was fixed by AWS in September 2025 following responsible disclosure on -
Google Gemini Prompt Injection Flaw Exposed Private Calendar Data via Malicious Invites
Source: The Hacker News | Published: 2026-01-19T17:21:00+00:00 | Score: 14.504
Cybersecurity researchers have disclosed details of a security flaw that leverages indirect prompt injection targeting Google Gemini as a way to bypass authorization guardrails and use Google Calendar as a data extraction mechanism.
The vulnerability, Miggo Security’s Head of Research, Liad Eliyahu, said, made it possible to circumvent Google Calendar’s privacy controls by hiding a dormant -
China-Linked Hackers Exploit VMware ESXi Zero-Days to Escape Virtual Machines
Source: The Hacker News | Published: 2026-01-09T17:43:00+00:00 | Score: 13.849
Chinese-speaking threat actors are suspected to have leveraged a compromised SonicWall VPN appliance as an initial access vector to deploy a VMware ESXi exploit that may have been developed as far back as February 2024.
Cybersecurity firm Huntress, which observed the activity in December 2025 and stopped it before it could progress to the final stage, said it may have resulted in a ransomware -
Black Basta Ransomware Leader Added to EU Most Wanted and INTERPOL Red Notice
Source: The Hacker News | Published: 2026-01-17T16:26:00+00:00 | Score: 12.993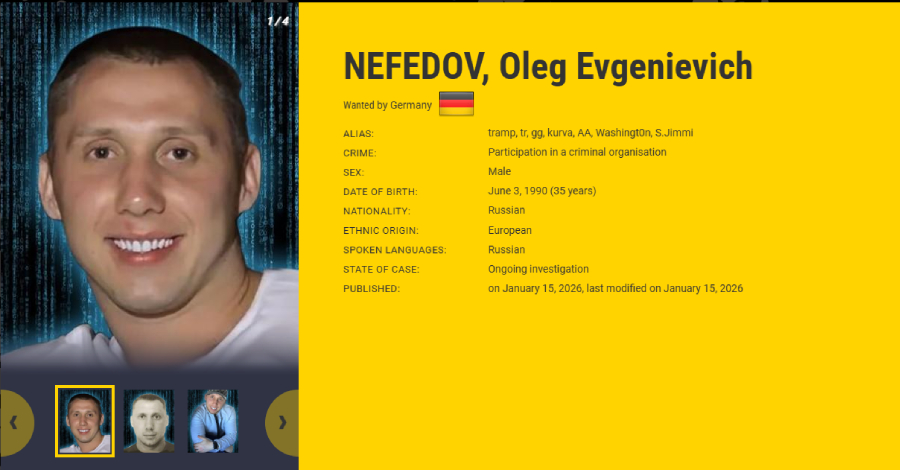
Ukrainian and German law enforcement authorities have identified two Ukrainians suspected of working for the Russia-linked ransomware-as-a-service (RaaS) group Black Basta.
In addition, the group’s alleged leader, a 35-year-old Russian national named Oleg Evgenievich Nefedov (Нефедов Олег Евгеньевич), has been added to the European Union’s Most Wanted and INTERPOL’s Red Notice lists, authorities -
Researchers Reveal Reprompt Attack Allowing Single-Click Data Exfiltration From Microsoft Copilot
Source: The Hacker News | Published: 2026-01-15T15:09:00+00:00 | Score: 12.917
Cybersecurity researchers have disclosed details of a new attack method dubbed Reprompt that could allow bad actors to exfiltrate sensitive data from artificial intelligence (AI) chatbots like Microsoft Copilot in a single click, while bypassing enterprise security controls entirely.
“Only a single click on a legitimate Microsoft link is required to compromise victims,” Varonis security
End of report.
